Introduction
Device whitelisting in PureAUTH is the process of allowing only authorized devices to access corporate resources and systems. This is achieved by creating a list of approved devices that are permitted to access the systems, and blocking all other devices. Learn more to know further about Device Access and Zero Trust access.
Admin Prerequisites
To implement Zero Trust Access Control in PureAUTH, there are two requirements:
- PureAUTH Admin Access: To configure and manage access controls, an administrator must have access to PureAUTH.
- User Device GUID: To verify the identity of a user device, PureAUTH requires a unique device GUID (Globally Unique Identifier). This is necessary to ensure that only authorized devices can access the network or system. The device GUID is typically OS generated identifier which cannot be changed.
User Prerequisites
To utilize AuthVR5, the following requirements must be met:
- AuthVR5 Desktop Application: To access the authentication features of AuthVR5, users must have the AuthVR5 Desktop application installed on their corporate device. If you don’t have it yet, visit our AuthVR5 page.
- Corporate Desktop/Laptop: To use the AuthVR5 Desktop application, users must have a corporate desktop or laptop. This is because AuthVR5 is designed to provide secure access to corporate resources and systems, and it requires a secure and trusted device.
To get the system Machine ID
- Windows :
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography" /v MachineGuidThis command will query the Windows registry for the "MachineGuid" value under the Cryptography key and display the GUID in the command prompt.
- Mac :
ioreg -rd1 -c IOPlatformExpertDevice -k IOPlatformUUID Copy IOPlatformUUIDThis command uses the “ioreg“ command to display the I/O Kit registry, which contains information about the system hardware and configuration.
- Linux :
cat /etc/machine-idThis command will display the contents of the /etc/machine-id file, which contains the machine ID of the system.
Device Whitelisting in PureAUTH
The following are the steps involved in device whitelisting in PureAUTH:
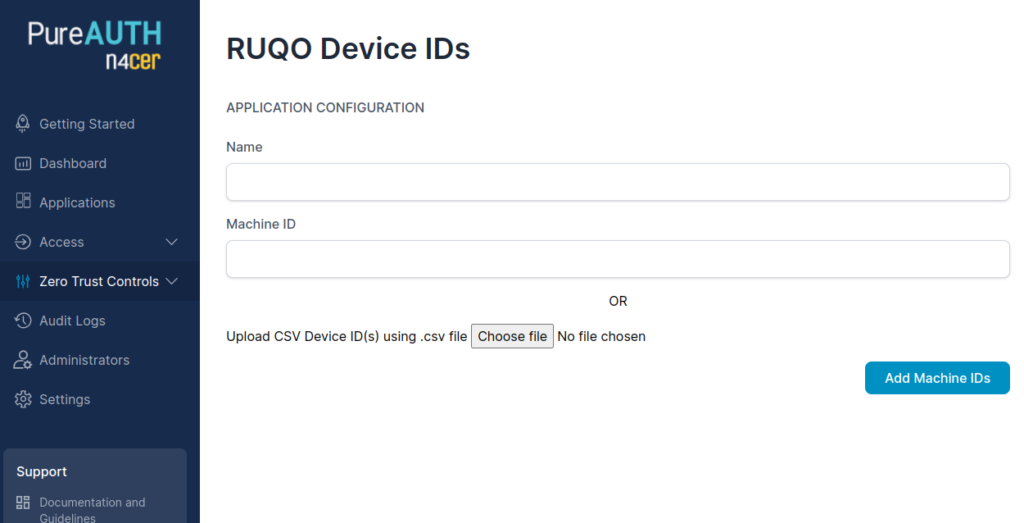
- Login to PureAUTH.
- In the navigation pane, go to Zero Trust Controls > Allowed Device List.
- Click on Add Device IDs.
- Enter Name : The name should be the user name that registers against the corporate device.
- Machine ID : To obtain the device machineID using the commands provided above.
- Click on Add Machine IDs to submit.
- You can use the following template to upload a list of machine IDs for bulk entry.
Restrict Applications to the allowed corporate device
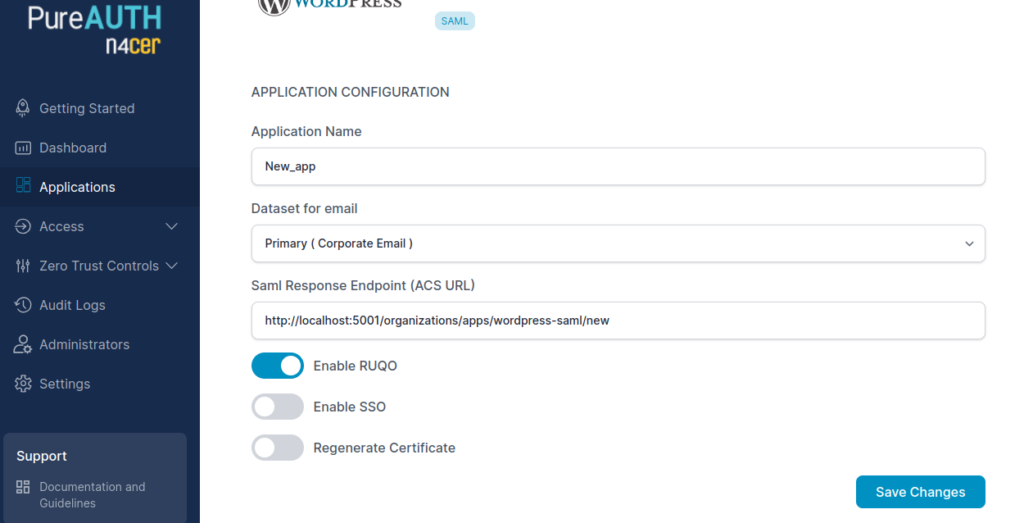
Here are the steps involved in restricting applications to allowed corporate devices.
- Login to PureAUTH.
- In the navigation pane, go to Applications.
- Open the application that you want to restrict.
- Click on Edit, right up corner.
- Click on toggle, Enable RUQO.
- Click on Save Changes.
Now the users will be able to access their applications only through the corporate device.
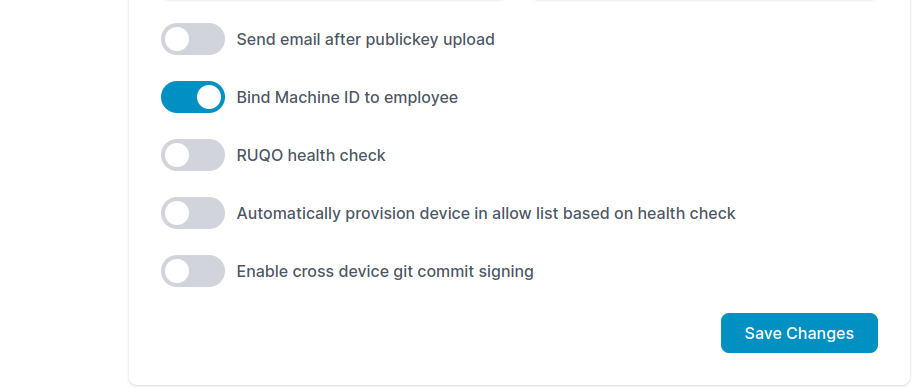
Bind Machine ID to employees
Once the option is enabled from the account settings, this feature will apply to all employees within the organization. When an employee logs in to their corporate device for the first time, they will be automatically bound to that device.
Here are the steps involved to enable bind machine ID to employee.
- Login to PureAUTH.
- In the navigation pane, go to Settings.
- In the Profile click on Edit, right up corner.
- Enable the toggle, Bind Machine ID to employee.
- Click on Save Changes.