Introduction
This document explains how to configure and manage GitLab On-Prem Omnibus integration with the PureAUTH Identity Platform and make GitLab authentication Passwordless.
The document includes the following steps:
- Add GitLab SAML application on the PureAUTH platform.
- Generate a fingerprint for an x509 certificate.
- Configure GitLab to use SAML authentication.
Add GitLab SAML application on PureAUTH
- Login to https://live.pureauth.io/organizations/login/
- Navigate to the Applications tab.
- Select “Add Application”.
- Select “GitLab”.
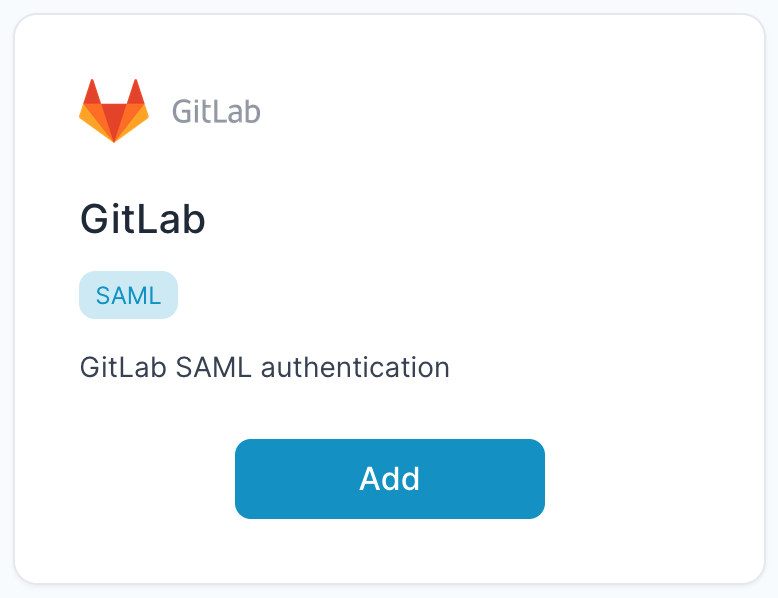
- Enter Any application Name.
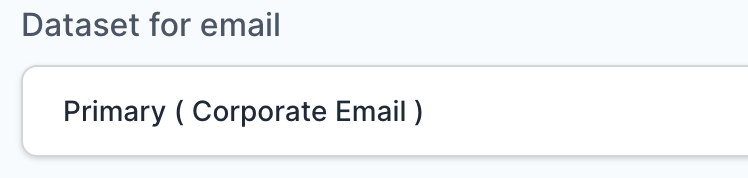
- Select Primary (Corporate Email) in the Dataset for email field.
- In “SAML Response Endpoint (ACS URL)” field, enter the URL using the following pattern.
https://<gitlab domain>/users/auth/saml/callback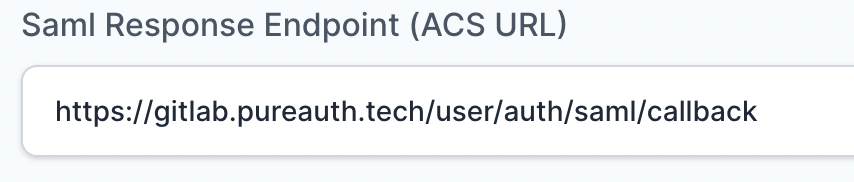
- In “Audience (Entity ID)” field, enter the URL using the following pattern.
https://<gitlab domain>/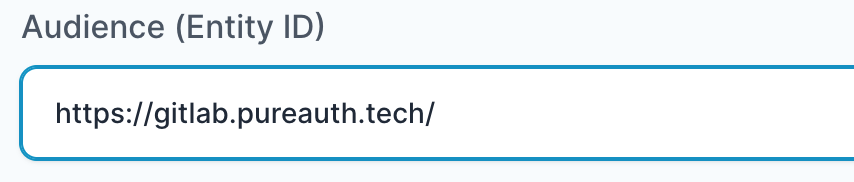
- Click the Add button.
- The application will be added and you will be shown SAML settings.
Note: Please also replace https with http whenever necessary (No SSL certificate is used)
Generate Fingerprint for the x509 certificate
- From the SAML Settings page, copy the X.509 certificate from
—–BEGIN CERTIFICATE—– to —–END CERTIFICATE—–.
- Go to https://www.samltool.com/fingerprint.php and paste it in the X.509 cert field.
- Click to “Calculate Fingerprint” option.
- Copy the Formatted Fingerprint and save it for later.
- E.g. 5F:80:F4:99:BB:3E:EA:1C:C7:E9:F3:89:9A:69:31:7A:66:FF:EA:43.
Configure GitLab to use SAML authentication
Access the Gitlab server and follow the commands below to configure SAML for GitLab:
- sudo editor /etc/gitlab/gitlab.rb
- [Optional]
To enable JIT user creation, add the following to the configuration file.
- gitlab_rails[‘omniauth_allow_single_sign_on’] = [‘saml’]
- gitlab_rails[‘omniauth_block_auto_created_users’] = false
You can automatically link SAML users with existing GitLab users if their email addresses match by adding the following setting:
- gitlab_rails[‘omniauth_auto_link_saml_user’] = true
- [SAML Configuration]
gitlab_rails['omniauth_providers'] = [
{
name: "saml",
label: "PureAUTH",
args: {
assertion_consumer_service_url: "https://<gitlab domain>/users/auth/saml/callback",
idp_cert_fingerprint: "<Generated Fingerprint from previous step>",
idp_sso_target_url: "<SAML LOGIN URL from PureAUTH>",
issuer: "https://<gitlab domain>/",
name_identifier_format: "urn:oasis:names:tc:SAML:2.0:nameid-format:persistent"
}
}
]
- Save the file and exit.
- Run sudo gitlab-ctl reconfigure
Testing PureAUTH
Go to the GitLab Login page, if you see a login with PureAUTH button, the configuration was successful.
Try to login to GitLab using your AuthVR5 application profile.
For more information, refer to the official GitLab documentation here.
Further Assistance
For further information or assistance, please contact PureID support team : support@pureid.io.