Introduction
This document explains how to integrate JSP with the PureAUTH Identity Platform and make JSP authentication passwordless.
Prerequisites
- Download java-saml toolkit from https://github.com/onelogin/java-saml
Configure Service Provider properties
- Navigate to samples/java-saml-tookit-jspsample/src/main/resources/onelogin.saml.properties
- Inside the onelogin.saml.properties file, you will find the following properties:
- onelogin.saml2.sp.entityid
- onelogin.saml2.sp.assertion_consumer_service.url
- onelogin.saml2.sp.single_logout_service.url
- Assign values to these properties based on your application.
- For the demo application, the base URL is http://localhost:8080/java-saml-tookit-jspsample/
So, the values are as follows:
- onelogin.saml2.sp.entityid = http://localhost:8080/java-saml-toolkit-jspsample/metadata.jsp
- onelogin.saml2.sp.assertion_consumer_service.url = http://localhost:8080/java-saml-toolkit-jspsample/acs.jsp
- onelogin.saml2.sp.single_logout_service.url = http://localhost:8000/java-saml-toolkit-jspsample/sls.jsp
Adding your JSP application on PureAUTH
- Visit https://live.pureauth.io/organizations/login/
- Enter your Organization ID or Organization Email
- You will receive an email on the organization’s email with a Login link.
- Click on the Login link, you will be logged in into the PureAUTH portal.
- Click on the Applications tab.
- And then click on the Add application button.
- You will see the list of applications, click on add Custom application.
An application form will appear after clicking on the Add button.
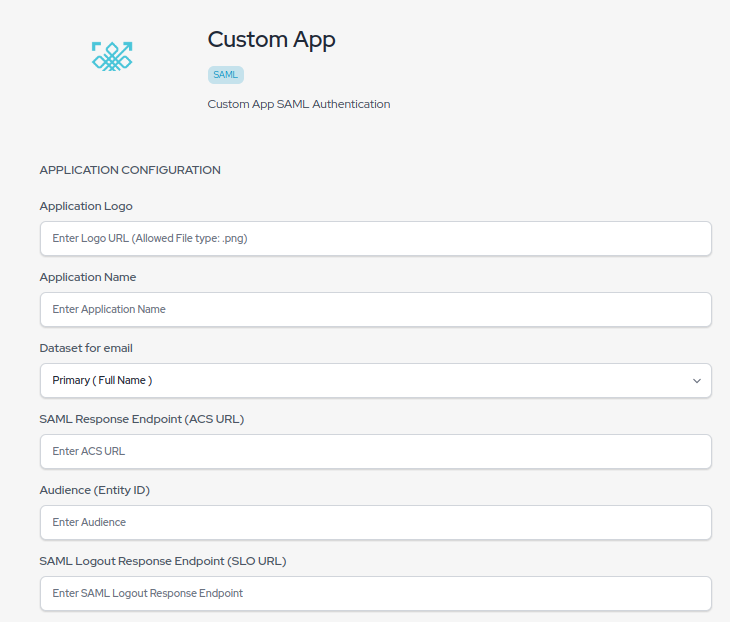
- Enter your application name
- Select Primary ( Corporate Email ) in Dataset for Email field
- Select Primary ( Full name ) in Dataset for Email field
- Go to the onelogin.saml.properties file of your application, copy the value of onelogin.saml2.sp.entityid and paste it into the “Audience (Entity ID)” text box.
- Copy the value of onelogin.saml2.sp.assertion_consumer_service.url and paste it into the “SAML Response Endpoint (ACS URL)” text box.
- Copy the value of onelogin.saml2.sp.single_logout_service.url and paste it into the “SAML Logout Response Endpoint (SLO URL)” text box.
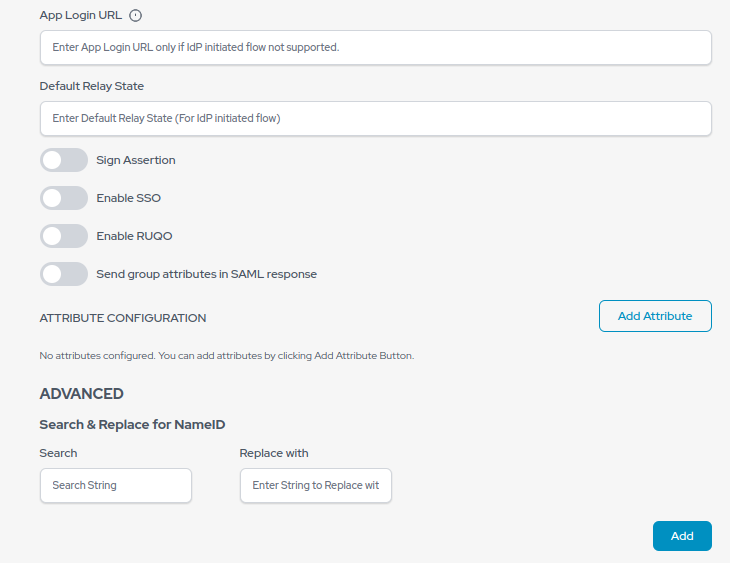
- Click on the Save button. Your application will be created once you click on Save.
- After clicking on Save button, Issuer URL (Entity ID), SAML Login URL, SAML Logout URL and X.509 Certificate will be generated.
Configuring SAML Single Sign-On on JSP application
- Navigate to samples/java-saml-tookit-jspsample/src/main/resources/onelogin.saml.properties
- Inside the onelogin.saml.properties file, you will find the following properties:
- onelogin.saml2.idp.entityid
- onelogin.saml2.idp.single_sign_on_service.url
- onelogin.saml2.idp.single_logout_service.url
- onelogin.saml2.idp.x509cert
- Copy the value from Issuer URL (Entity ID) on the PureAUTH portal and assign the value to onelogin.saml2.idp.entityid in the onelogin.saml.properties file.
- Similarly, copy the value from SAML Login URL on the PureAUTH portal and assign it to onelogin.saml2.idp.single_sign_on_service.url
- Copy the value from SAML Logout URL on the PureAUTH portal and assign it to onelogin.saml2.idp.single_logout_service.url
- Copy the value from X.509 Certificate on the PureAUTH portal and assign it to onelogin.saml2.idp.x509cert
